AnMaXX, Gerber EDV and the Qrypter Connection
Published on 9th April 2018, 10:03:17 UTC
In August 2017, I've blogged about Adwind, a cross-platform RAT written in Java that is also known as "jRAT" and "JSocket". The main infection vector for Adwind is via spoofed email. The attacker doesn't have to care about the recipients operating system (OS): Adwind works on Windows, macOS and Linux.
Recently, security researchers and AV vendors have published a handful interesting blog posts on Adwind. The recent uprise in Adwind campaigns seems to be related to Qrypter: a Malware-as-a-Service (MaaS) platform @Angelill0 blogged about in December 2017. The Qrypter MaaS platform is hosted in the Tor network, which makes it more resilient against takedowns and actions from law enforcement (LEA). However, the botnet controllers itself are hosted in the clear net. The following map shows the top Adwind C&C hosting countries in the past 6 months. In this period I've spotted almost 10'000 Adwind samples calling out to more than 2'800 distinct botnet controllers (C&Cs). Most of these Adwind samples are related to the Qrypter MaaS.
Looking at the top Adwind botnet C&C hosting countries, we can see that they are mostly hosted in the United States (US), followed by Netherlands (NL) and Great Britain (GB):
In my blog post on Adwind in August 2017, I've mentioned AnMaXX. AnMaXX was (and still is) one of the networks which is hostings a vast majority of the Adwind C&Cs. However, it's not just AnMaXX. A few days after I've published my Adwind blogpost I've came across another network called Gerber EDV-Dienstleistungen (aka gerber-edv.net). During my investigation, the network quickly raised my attention: Gerber EDV has, just like AnMaXX, no web site:
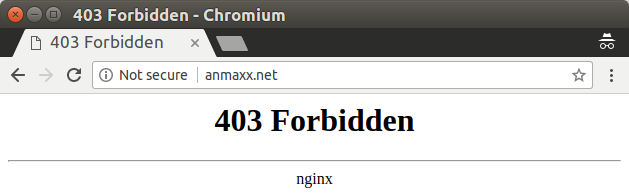
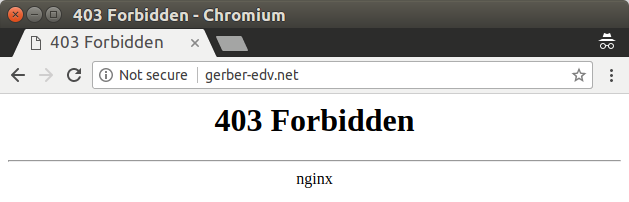
But not just that raised my suspicion. The fact that both, Gerber EDV and AnMaXX are hosted on the same IP address and even use the same mailserver (MX) doesn't make the situation any better:
anmaxx.net A 78.47.229.243
gerber-edv.net A 78.47.229.243
;; QUESTION SECTION:
;mx.anmaxx.net. IN A
;; ANSWER SECTION:
mx.anmaxx.net. 599 IN A 78.47.229.243
;; QUESTION SECTION:
;mx.gerber-edv.net. IN A
;; ANSWER SECTION:
mx.gerber-edv.net. 599 IN A 78.47.229.243
Is it possible that Gerber EDV is operated by the same guys as AnMaXX? It indeed seems so. The said IP address is also hosting another domain name: rivavpn.com
Taking a closer look at the netranges of Gerber associated with Qrypter reveals that they have one thing in common: They are all labeled with "Gerber non logging VPN Service". So it appears that Gerber sells VPN services, but I'm wondering how Gerber EDV advertises and sells their VPN services as their domain name doesn't host any website (uh?). As Gerber EDV-Dienstleistungen has their offices in Switzerland, I decided to vist them and ask them where all this abuse related to Adwind / Qrypter is coming from.
% Information related to '91.192.100.1 - 91.192.100.63'
% Abuse contact for '91.192.100.1 - 91.192.100.63' is 'abuse@gerber-edv.net'
inetnum: 91.192.100.1 - 91.192.100.63
netname: Gerber_non-logging_VPN_service
country: CH
admin-c: JG8768-RIPE
tech-c: JG8768-RIPE
org: ORG-GE100-RIPE
abuse-c: GE2550-RIPE
status: ASSIGNED PA
mnt-by: MNT-DA327
created: 2017-11-14T13:09:30Z
last-modified: 2017-11-15T08:57:40Z
source: RIPE
organisation: ORG-GE100-RIPE
org-name: Gerber EDV-Dienstleistungen
org-type: OTHER
remarks: ****************************************************
remarks: Spamhaus, please note:
remarks:
remarks: THIS IP ADDRESS BELONGS TO A NON-LOGGING VPN SERVICE
remarks:
remarks: For further information please contact:
remarks:
remarks: abuse@gerber-edv.net or notification@gerber-edv.net
remarks:
remarks: Thank you.
remarks: ****************************************************
address: Junkerngasse 44, 3011 Bern, Switzerland
abuse-c: GE2550-RIPE
mnt-ref: GERBER-MNT
mnt-ref: MNT-DA327
mnt-by: GERBER-MNT
mnt-by: MNT-DA327
created: 2017-11-04T22:44:21Z
last-modified: 2017-11-09T11:29:29Z
source: RIPE # Filtered
After a 1 1/2 hours train ride, I finally arrived in Bern. Gerber has their offices at Junkerngasse 44, which is in walking distance from the train station. So I decided to take a short walk:

After a 10 minutes walk I arrived at Junkerngasse 44 where Gerber supposes to have their office. It is a nice building in the old town of Bern. Actually, not a cheap place for renting an office. Will I find Gerber EDV here? I started having doubts...

Number 44. That must be it. But checking the sign at the front reveals: There is no Gerber EDV in this building. A quick cross check on the phone book proofs what I just saw: No Gerber EDV at this address:
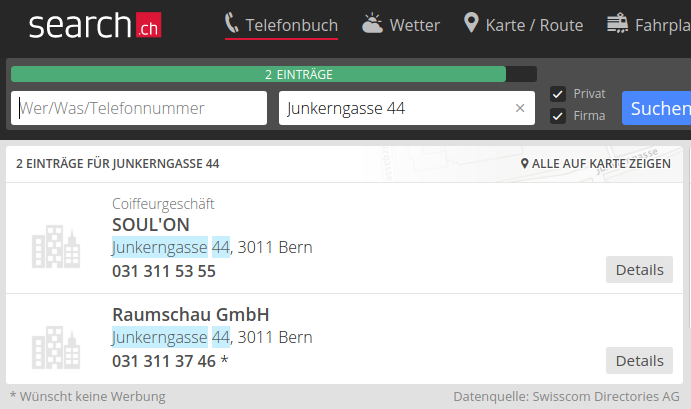
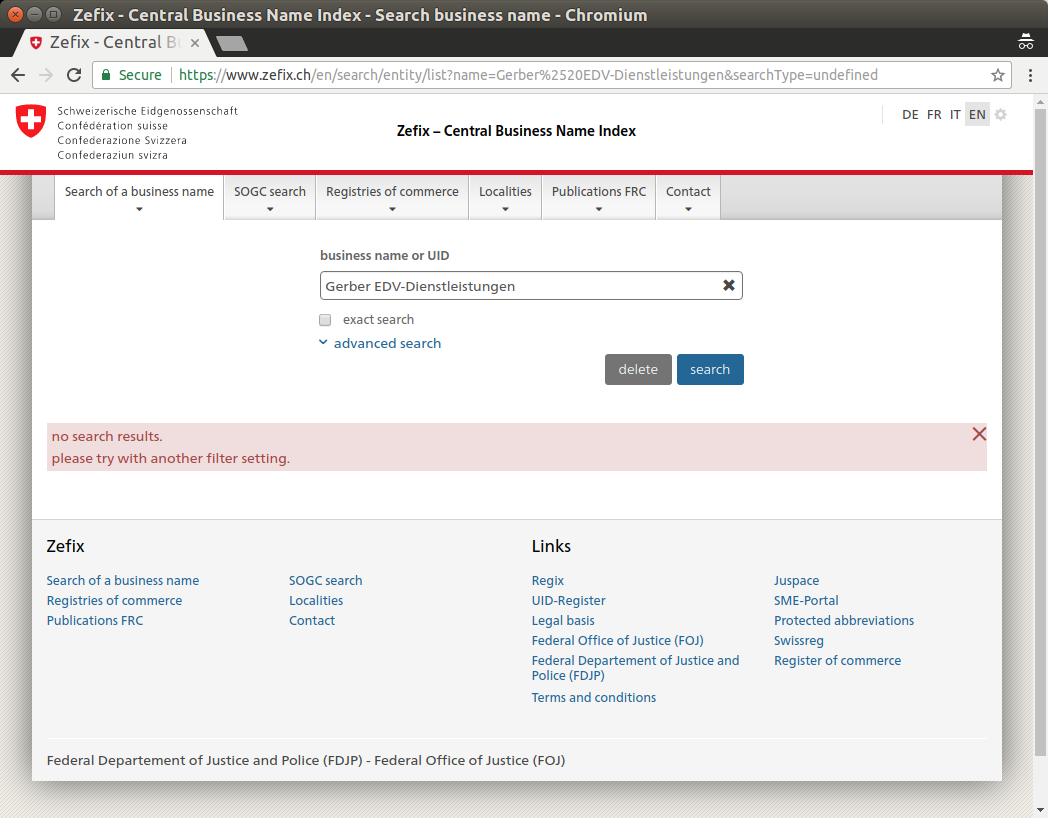
As it might be possible that Gerber EDV moved their offices to a different location and forgot to update their RIPE record accordingly (actually, that's something I am confronted with very often: outdated RIPE records), I decided to have a quick look at the Central Business Name Index (Zefix) of the Federal Office of Justice. However, there is no registered company under that name in Switzerland:
Conclusion
Gerber (as well as AnMaXX) seems to be all fake. It is obviouse that both are operated by the same guys. There is no Gerber EDV-Dienstleistungen at Junkerngasse 44 in Bern and not even a registered company with that name in Switzerland. The sole purpose of Gerber and AnMaXX seems to be providing botnet hosting to Qrypter MaaS and other RATs such as NanoCore and RemcosRAT. I've also learned that RIPE requires that the information provided in the RIPE objects is correct. However, RIPE does not verify the provided information at all. I've submitted a complaint to RIPE regarding the incorrect information provided by Gerber EDV in the hope that RIPE can force them to reveal their real location (if there is any).
If you are a network- or sysadmin, I highly recommend you to block any incoming and outgoing traffic towards the follow prefixes that are owned / maintained by either Gerber EDV, AnMaXX or rivavpn.com:
78.130.176.160/27 gerber-edv.net AS9070
78.130.176.192/27 gerber-edv.net AS9070
91.192.100.0/26 gerber-edv.net AS51395
185.208.211.0/24 gerber-edv.net AS205406
185.209.85.64/28 gerber-edv.net AS57695
185.209.85.176/28 gerber-edv.net AS57695
185.227.83.32/27 gerber-edv.net AS205406
194.68.59.0/25 gerber-edv.net AS8473
77.48.28.192/26 anmaxx.net AS6830
79.134.225.0/26 anmaxx.net AS6775
89.35.228.192/26 anmaxx.net AS34304
95.140.125.0/25 anmaxx.net AS9125
95.167.151.224/27 anmaxx.net AS12389
146.255.79.160/27 anmaxx.net AS34547
154.16.63.0/24 anmaxx.net AS50841
154.16.201.0/24 anmaxx.net AS200995
154.16.220.0/24 anmaxx.net AS56630
176.10.124.192/26 anmaxx.net AS51395
181.215.247.0/24 anmaxx.net AS57944
185.101.34.64/26 anmaxx.net AS34989
185.140.53.0/24 anmaxx.net AS24961
185.145.44.0/24 anmaxx.net AS50113
185.145.45.0/24 anmaxx.net AS49981
185.158.139.0/24 anmaxx.net AS31103
191.101.22.0/24 anmaxx.net AS62240
213.183.40.0/26 anmaxx.net AS56630
213.183.58.0/26 anmaxx.net AS56630
5.133.11.56/29 anmaxx.net AS197155
5.133.11.224/27 anmaxx.net AS197155
5.187.48.32/29 anmaxx.net AS197155
5.187.49.224/29 anmaxx.net AS197155
5.133.15.0/29 anmaxx.net AS197155
178.255.40.136/30 anmaxx.net AS197155
81.95.126.128/26 anmaxx.net AS42160
173.46.85.0/24 rivavpn.com AS6775
In addition, I've seen the following netranges involved in massive Adwind botnet C&C hosting too, but couldn't map them to Gerber EDV or AnMaXX. I recommend you to block them as well on your network perimeter:
204.152.219.64/26 sklepkibicakonskie.pl AS8100
174.127.99.128/25 sklepkibicakonskie.pl AS36351
23.227.207.128/25 swiftway.net AS35017
154.16.93.160/27 host1plus.com AS37692
184.75.209.160/27 amanah.com AS32489
212.7.208.0/24 dediserv.eu AS60781
212.7.218.0/24 dediserv.eu AS60781
216.38.8.160/27 gigenet.com AS32181
67.215.4.64/28 globo.tech AS36666
79.172.242.0/25 webenlet.hu AS29278
213.184.126.128/27 netstyle.io AS199267
23.105.131.128/25 nobistech.net AS396362
The mentioned networks are not just used to host Adwind / Qrypter C&Cs, they also host plenty of other botnet controllers associated with dozens of different RATs and malware families, such as RemcosRAT, NanoCore and many more. If you want to convince yourself, you may want to take a look at the following list of 5'000+ botnet C&Cs I've seen in the past years being hosted in these networks:
More information about Qrypter MaaS can be found here: