Introducing: abuse.ch’s Hunting Platform
Published on 11th March 2025, 14:11:35 UTC
Community lies at the heart of everything we do. For over 15 years, we have provided actionable cyber threat intelligence through community-driven platforms - completely free of charge. We’re truly committed to putting the community first.
Over time, the number of platforms we operate has grown, to seven distinct platforms, each providing unique benefits in the fight against cyber threats. However, the challenge of searching through each platform for comprehensive threat information has always remained. But that's about to change...
No more platform-hopping!
Introducing: abuse.ch’s Hunting Platform. Now, cyber security experts and threat hunters can query all our datasets from one place, with one query. This includes data from:
- URLhaus – a malware URL tracking platform
- MalwareBazaar – a malware sharing platform
- ThreatFox – an indicators of compromise (IOC) sharing platform
- YARAify – a crowd-sourced YARA scan engine
You can also query abuse.ch datasets that have never been made publicly accessible before! These are:
- Sandnet – our internal malware detonation service
- IPintel – our internal IP address signal collection service
- ProxyCheck – database of known residential proxy IP addresses
False positives happen
With all this community-driven data, false positives are inevitable, and we want to be transparent about them. Therefore, we have launched a consolidated False Positive List. This list provides users with an easy way to identify and access false positives generated on our platforms. It can be accessed through the hunting platform and is available via API (CSV or JSON data export).
But that’s not everything. We are delighted to share even more new features, on our existing platforms, aimed at making your life easier when hunting cyber threats.
Let's see what's NEW on our existing platforms
URLhaus
Payload overview: You can now access payloads retrieved by URLhaus from malware URLs via a dedicated "Payloads" tab. This tab is available on the main page when browsing recent URLs and in the host section when investigating malware hosts.
Trigger a URL rescan: You can now trigger an immediate rescan of any URL tracked by URLhaus. Simply click the "Rescan" button when browsing a URL, and it will trigger an immediate rescan while fetching the most recent payload from the site.
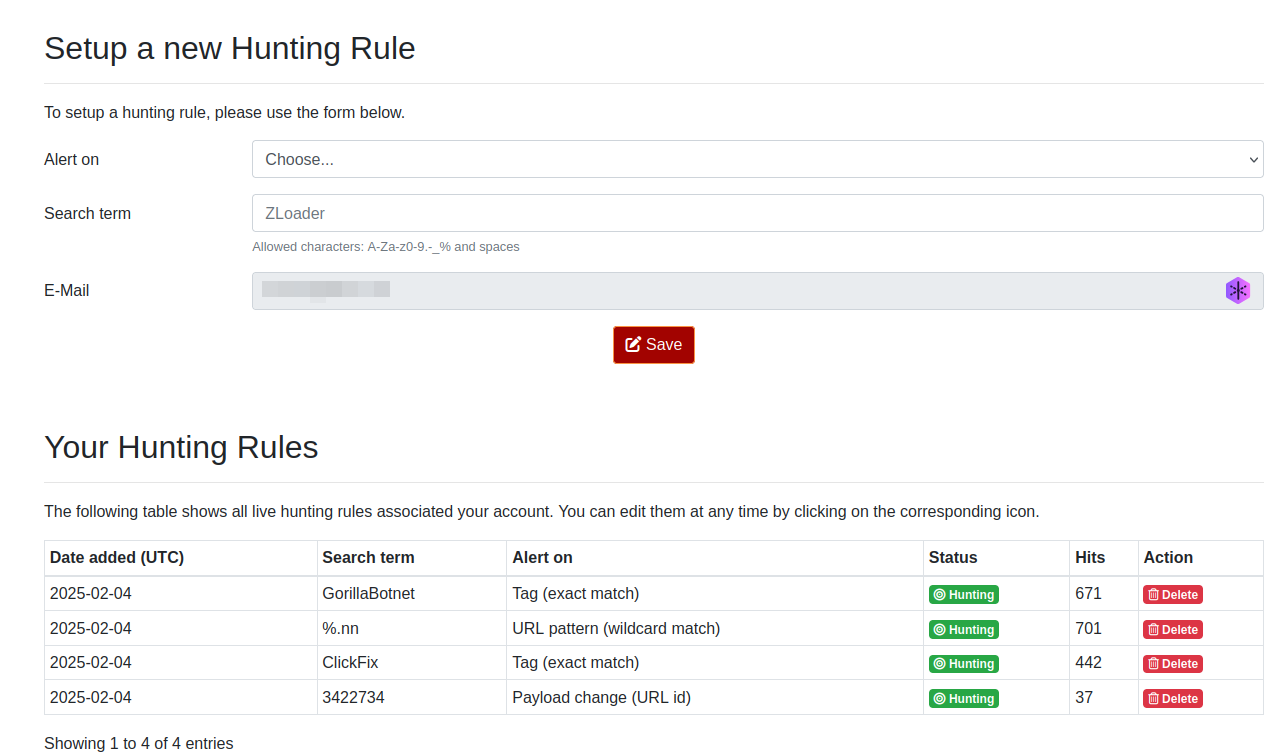
URLhaus hunting alerts: URLhaus now offers an alerting functionality, similar to MalwareBazaar and ThreatFox. This new feature allows you to set up notifications for the following events:
- A new URL reported to URLhaus matches a specific pattern (wildcard match).
- A URL is tagged with a specific label.
- A payload associated with a particular malware family (signature) or a specific URL tracked by URLhaus serves a new payload.
YARAify
Auto-delete files after scanning: When submitting a file to YARAify, you can now choose to have it automatically deleted after scanning. If this option is enabled, YARAify will remove the raw file after 7 days, while scan results and metadata remain accessible.
Trigger a file rescan: Previously, rescanning a file on YARAify required re-submitting it. To streamline this process, we’ve introduced a simple rescan feature that allows you to trigger a rescan for files already on YARAify. This feature is also accessible via the YARAify API. You can find a sample Python 3 script in our public GitHub repository.
Deploy YARA rules via the API: Until now, YARA rules on YARAify could only be deployed via the web UI. We've introduced a new API endpoint that lets you deploy YARA rules directly through the YARAify API. You can find a sample Python 3 script for deploying YARA rules in our public GitHub repository.
ThreatFox
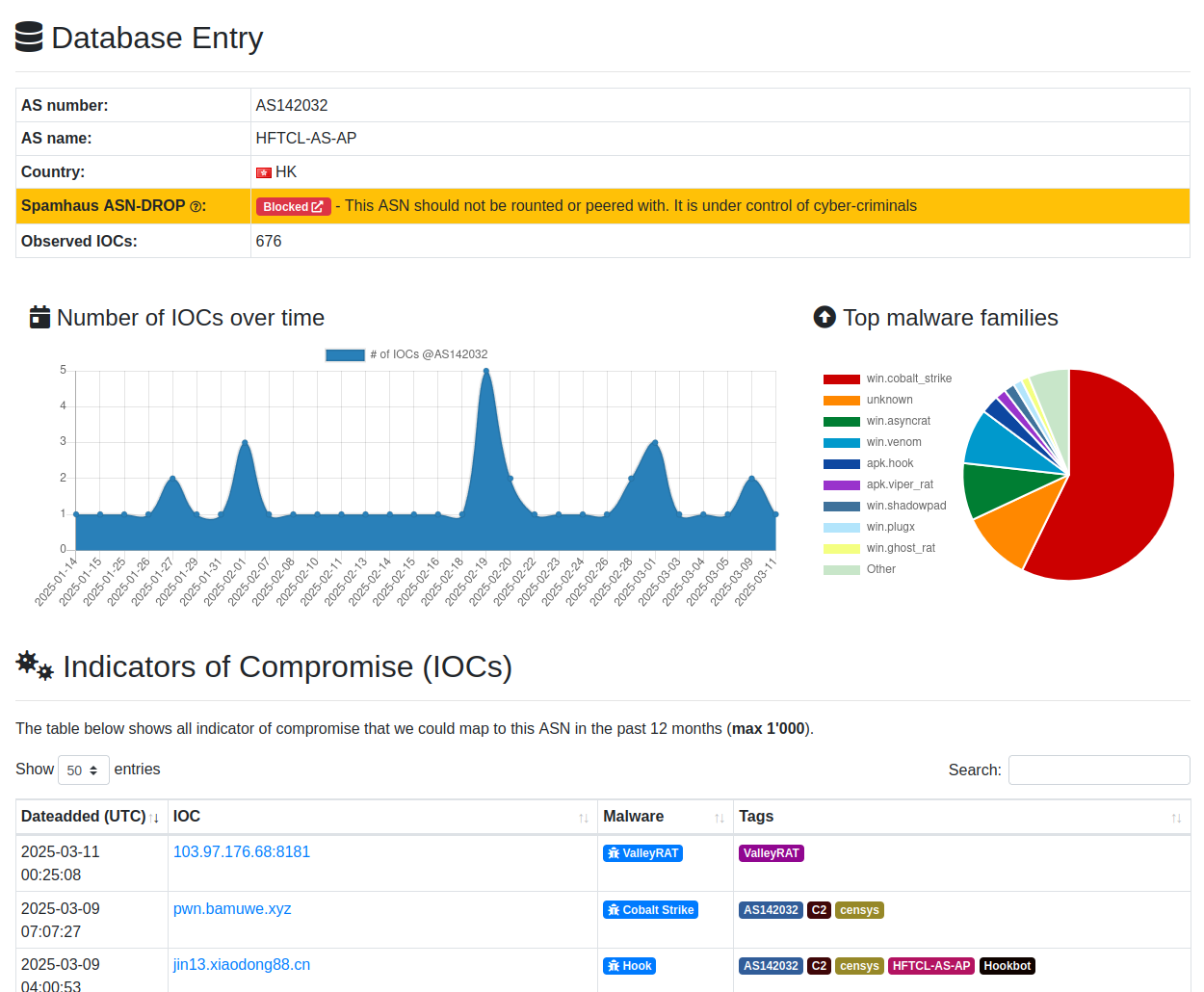
ASN information and statistics: When you browse a network-based IOC on ThreatFox (such as a domain, IP, or URL), the platform will now provide information about the associated network operator (ASN). From there, you can do a deep dive into a specific network, gaining insights into IOCs and statistics associated with a particular ASN.
Here’s an example: AS142032 HFTCL-AS-AP
MalwareBazaar
Bash (shell) script parser: When you submit malicious Bash (shell) scripts to MB, we will now try to automatically extract potential payload delivery URLs and prominently display them on the malware sample report page.
Here’s an example: real.sh (Mirai)
Too much information? We know there is a lot to digest in this blog post. That’s why, we recently held a live demo of the newest features of our hunting platform - watch it here.
Psst... even more features coming soon!
Yes, you read that right. It doesn't end here! New, cool features are coming to the abuse.ch Hunting Platform in the coming weeks - for everyone, for FREE! Stay tuned and follow us on your preferred social media channel to stay updated: Mastadon, Bluesky, LinkedIn, or X.
Contribute to our platforms and help make a difference!
Do you want to share cyber threat intelligence with a bigger audience and make a real impact on cybersecurity? Join our growing community of cyber security experts and threat hunters, and:
- Share active malware distribution sites with URLhaus
- Share confirmed malware samples on MalwareBazaar
- Share indicators of compromise (IOCs) on ThreatFox
- Leverage YARAify to identify suspicious or malicious files
To learn more about how your contributions impact cyber security and internet security, check out the following blog post: abuse.ch & Spamhaus: The impact of your contributions.