Cybercriminals taking advantage of Cryptocurrency Boom
Published on 8th January 2018, 11:22:59 UTC
It is fair to say that 2017 was the year of cryptocurrencies. In 2017, many cryptocurrencies went through the roof. Let's take Bitcoin (BTC) as an example: 1.0 BTC got traded for about 1,000 USD in beginning of 2017. In December 2017, one Bitcoin was more than 18,000 USD worth. An increase of 1800%! It was a very successful year for traders speculating on cryptocurrencies, and even more for cybercriminals: Cryptocurrencies like Bitcoin are the #1 means of payment when it comes to extortions.
In the past years, the amount of extortions in cyberspace has grown rapidly. The most popular (and likely most easiest) way to extort money from not only random internet users but also small and medium businesses (like webshops) is DDoS extortion (DD4BC, Armada collective, you name it) and Ransomware (Crypt0L0cker, Locky, Cerber etc). Many of them demand Bitcoins as a ransom. The amount of demanded Bitcoins varies, but goes up to 10 BTC and more. For example, in 2015, the Armada Collective was blackmailing Swiss Hosting Providers, demanding 10 BTC. Back than, 10 BTC were traded for about 2,500 USD. Now, if we assume that just one victim paid the ransom and the attackers had not cashed out the money yet, they would have had more 160,000 USD by end of 2017. And that with almost 0 efforts. Not bad!
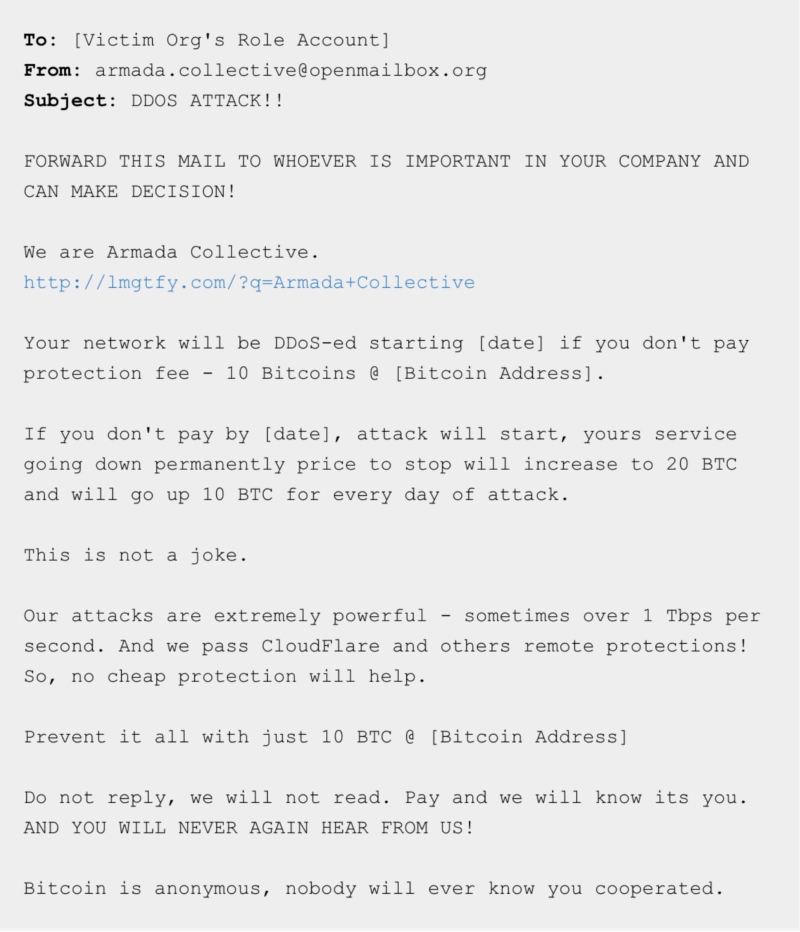
Source: https://blog.nsfocusglobal.com/categories/armada-collective-ddos-attack/
2017 was not only a very successful year for cybercriminals blackmailing internet users. In the second half of 2017, I've noticed a massive increase of cryptocurrency miners (CoinMiners), abusing malware infected machines to mine Bitcoins and other cryptocurrencies. In July 2017, the number of malware samples I've seen mining cryptocurrencies started to increase from almost 0 up to 1,200 per month. The following chart shows the number of malware samples involved in mining cryptocurrencies (so called miners) and the Bitcoin price (BTC/USD):
Cybercriminals who have mined Bitcoins between September and November using infected computers could more than double their revenue in December 2017.
CoinMiners like noobLoader.net or XMRig are commonly getting installed on the victims machine by droppers, such as Neutrino or Smoke Loader. Unlike ebanking trojans like Gozi or PandaZeuS who are trying to steal money from the victims bank account, the only harm that a CoinMiner causes to you and your computer is that the infected machine gets very slow (as the CPU is busy with the mathematical operations that are neccessary in order to earn bitcoins). But as many CoinMiners are finding its way on the victims machine through droppers, it is likely that your computer has other malware installed too. For example, I've seen a Smoke Loader campaign dropping Neutrino, Citadel, Gozi and a CoinMiner just at the same time. Poor victim who gets all that crap installed on his computer!
The screenshot below documents a Neutrino campaign that is dropping a CoinMiner on the infected machine.
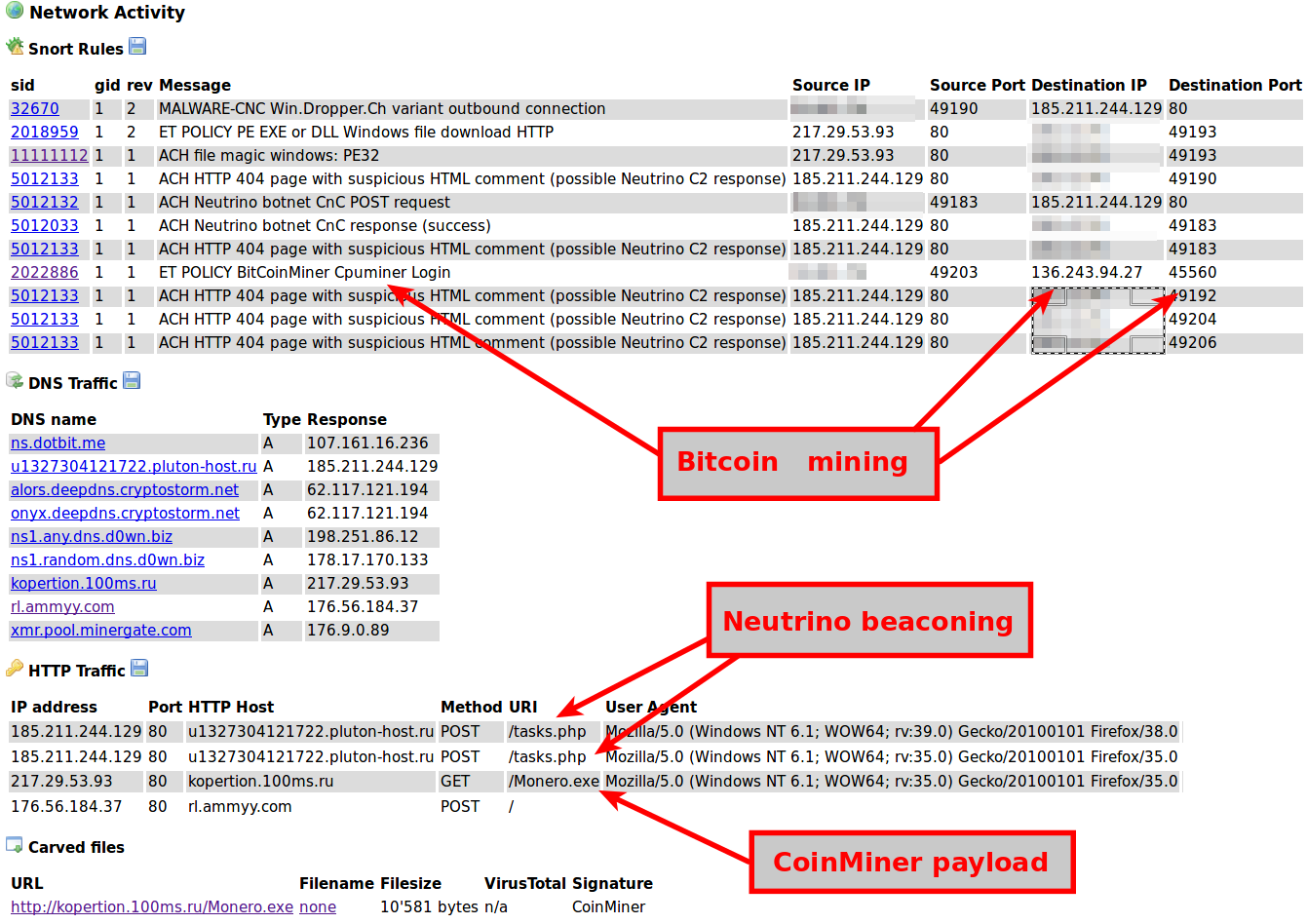
As you can imagine, extortionist, malware authors and botnet herders are not the only ones who want to gain profit from the boom of cryptocurrencies. Speaking about the Swiss spam landscape, I've see an increase of spam campaigns promoting suspect online trading platform. The goal of these spam emails is commonly the same: trying to convince the recipient of the spam email to register themselves on the promoted online trading platform by promising them an horrendous profit from invested money. Below is a spam sample I've just recieved in the beginning of January 2018 in one of my spam traps.
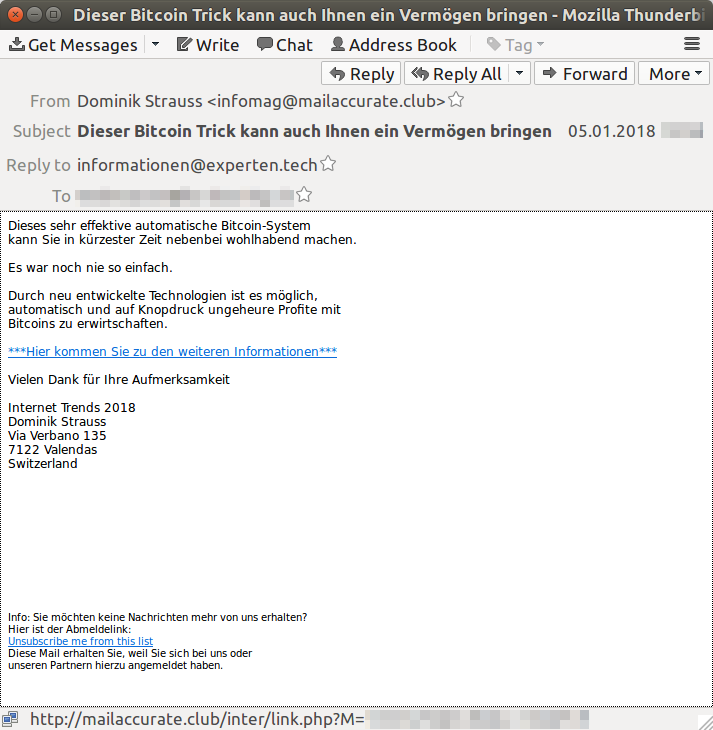
These spam campaigns are usually being sent out from /24 netblocks, using Snowshoe techniques. For example, the spam email above was sent from 196.53.95.159 which is associated with a hosting company called LogicWeb Inc. located in South Africa (ZA). Looking at the neighborhood of the said IP address shows that the whole /24 is being used for sending out spam emails.
The spam email itself pretends to come from non-existent Swiss companies called "Internet Trends 2018". Following the hyperlinks in such spam emails will lead you to websites like thecryptosoftware.co, kryptohandel.trade or universemarkets.com. The purpose of these online portals is unknown. Googleing a bit around reveals that they might be involved in so called pyramid scheme or that they are just completely fake.
I'm sure the use of Bitcoin and other cryptocurrencies in cybercrime operations will not drop unless the worth of cryptocurrencies falls down dramatically too. I do believe that we will see even more cybercrime operations in the future taking advantage of cryptocurrencies.
Further reading: